ICS SIGHT
Asset and Vulnerability Management
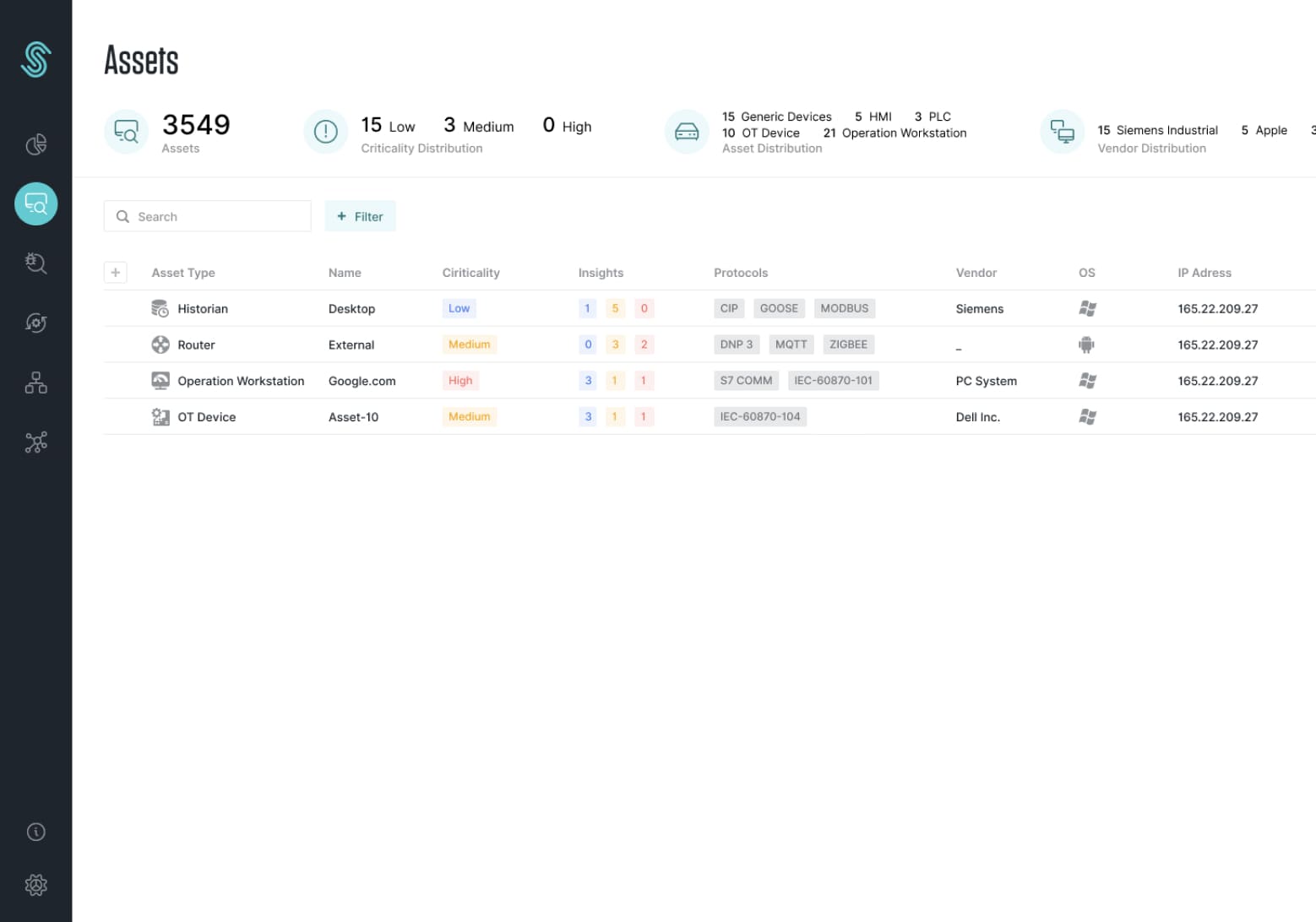
Get long-lasting and high-performance systems with asset management
In general, asset management is a systematic process performed to achieve the highest possible performance in terms of longevity and efficiency. It is important not only in terms of cyber security but also for the smooth running of the process in the industry. It is provided by passive listening of the network in the industry and separating the protocols with advanced technologies. Assets in SCADA systems can generally be devices such as PLC, HMI and RTU or switch, router and operator computers’ network components.
The next stage of asset management is to identify published vulnerabilities in that international vulnerability database, based on information such as firmware or serial number of the assets in question. Obtaining said device’s information from the network with passive listening requires using highly advanced engineering techniques. However, SCADA systems take into consideration as completely offline systems and the vulnerability database is updated regularly while it is always available for use within ICS Sight.
Identify your weak points and keep your assets safe with weakness management
ICS SIGHT
OT Protocols and Devices Are Our Expertise
With our years of work and experience on OT protocols (Modbus, DNP3, CIP, S7Comm etc.) and devices (PLC, HMI, RTU, IED etc.) used in SCADA networks, we monitor all of your assets completely with their communications.

Extensive IT/OT/IIOT Protocol and Vendor Support
Effective asset management is offered for all industries with more than 30 IT/OT/ IIOT communication protocols and dozens of manufacturer support.
Detailed Asset Information Analysis
In addition to the IP and MAC addresses of the assets, detailed features such as firmware, serial number, operating system, installed programs and additional module information are detected.
Rich and Up-to-Date Database
The weaknesses of the assets are revealed to be eliminated with the regularly updated weakness management mechanism with the offline working capability.
PRODUCTS
You Can Browse Our Other Features
Rule Engine
The rule engine which has strong cyber security rules that can detect thousands of harmful software and attack types, can be configured for the businesses with the rules that can be added by the user in a simple way.
Anomaly Detection
The warning system, in which anomaly detection and detection anomalies are shown with the rule engine, is designed quite flexibly not only for cyber attacks with ready rules but also for detection of protocol and device-based anomalies.
Network Mapping
The network map provides a lot of detailed information such as the location of the assets, communication between the assets, possible attack vectors and spoken protocols, as it shows the overall structure of the system.