ICS SIGHT
Smart Process Management
With the smart process management, track all of the process and the process data closely
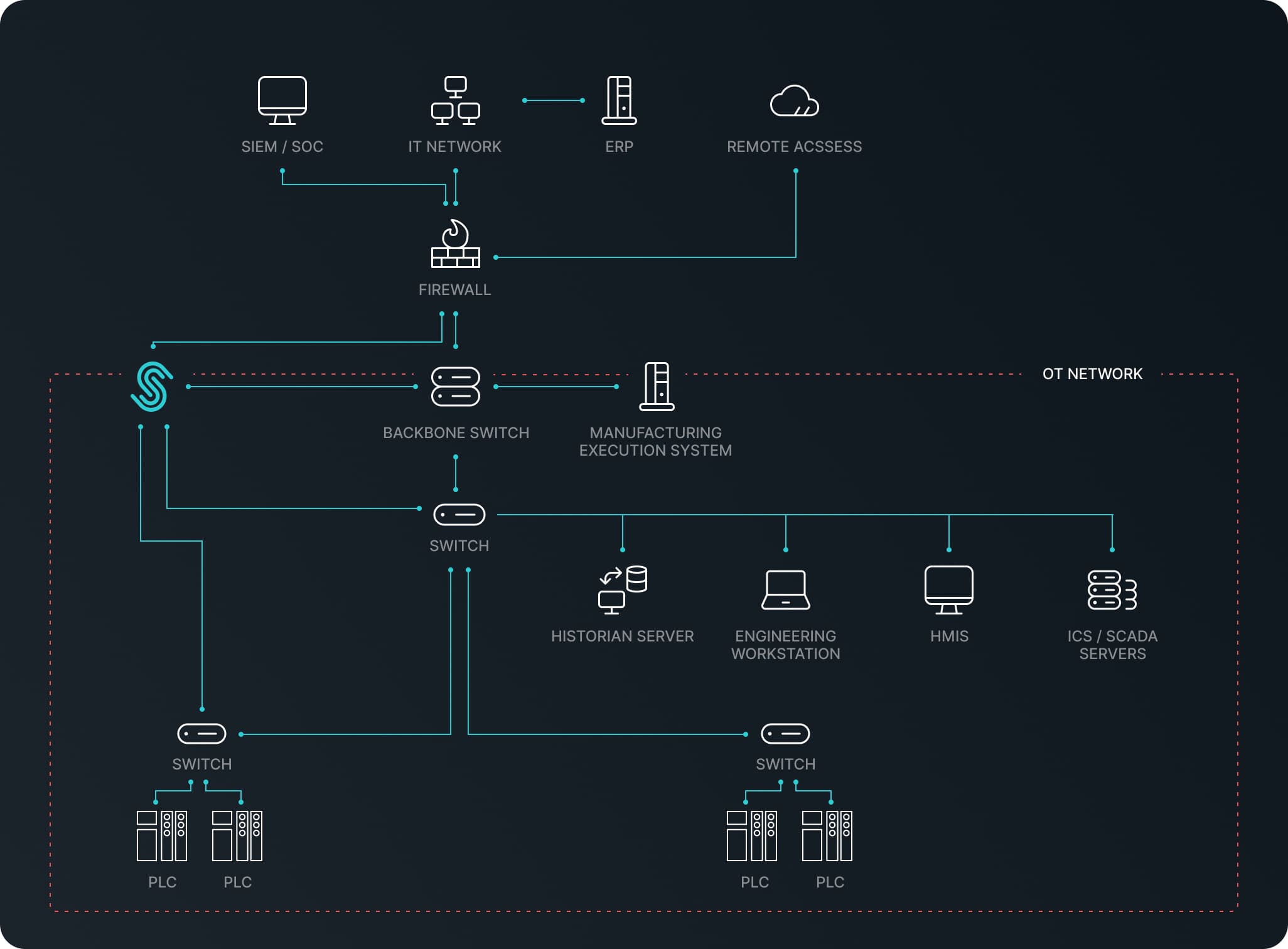
Process is the most important concept in critical infrastructures. It is vital to closely monitor the current process in the industry, to detect abnormal process data between devices and to report these actions to SCADA operators instantly. Accurate capture of process data is only possible if the network features and communication protocols are fully supported. As the ICS Defense team, we know the industrial systems very well, understand your sensitivities and consider them while we offer you a comprehensive management and cyber attack detection system about the process data in your business.
ICS PRODUCT
We Know the Importance of Your Process and We Understand Your Sensitivity
Every industry has its own sensitivities. While energy companies prioritize the uninterrupted continuity of energy, the continuity of the kiln is essential for cement enterprises. We understand both you and your concerns, and we pay particular attention to developing our product with the same precision.
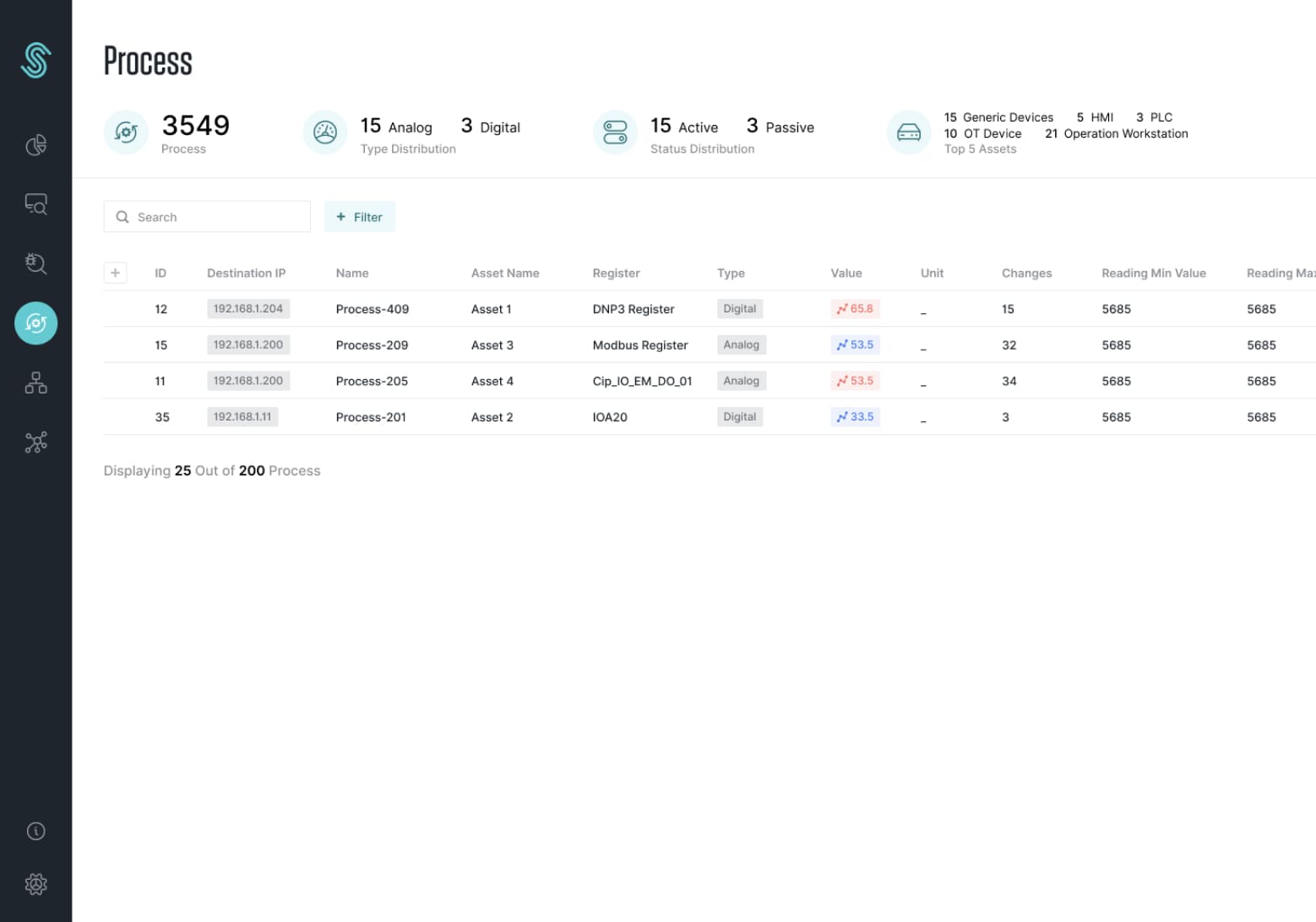
Smart Process Tracking and Graphical Analysis
Process data is tracked with artificial intelligence and machine learning in terms of both the time cycle and the value of the data. In addition, all historical data is presented to the users graphically for analysis.
Determination of The Safety Range
Process-specific security intervals can be specified easily to generate an alarm as soon as the process data that needs to pass within a certain interval goes out of range. Then, as soon as the data passing in the system goes out of this range, an alarm is generated and the operator is warned.
Function-Specific Rule’s Writing
Some function codes of OT protocols indicate a problem in the process. A rule can be written easily to capture process-based function codes like these.
PRODUCTS
You Can Browse Our Other Features
Rule Engine
The rule engine which has strong cyber security rules that can detect thousands of harmful software and attack types, can be configured for the businesses with the rules that can be added by the user in a simple way.
Anomaly Detection
The warning system, in which anomaly detection and detection anomalies are shown with the rule engine, is designed quite flexibly not only for cyber attacks with ready rules but also for detection of protocol and device-based anomalies.
Network Mapping
The network map provides a lot of detailed information such as the location of the assets, communication between the assets, possible attack vectors and spoken protocols, as it shows the overall structure of the system.