ICS SIGHT
Anomaly Detection with Advanced Rule Engine
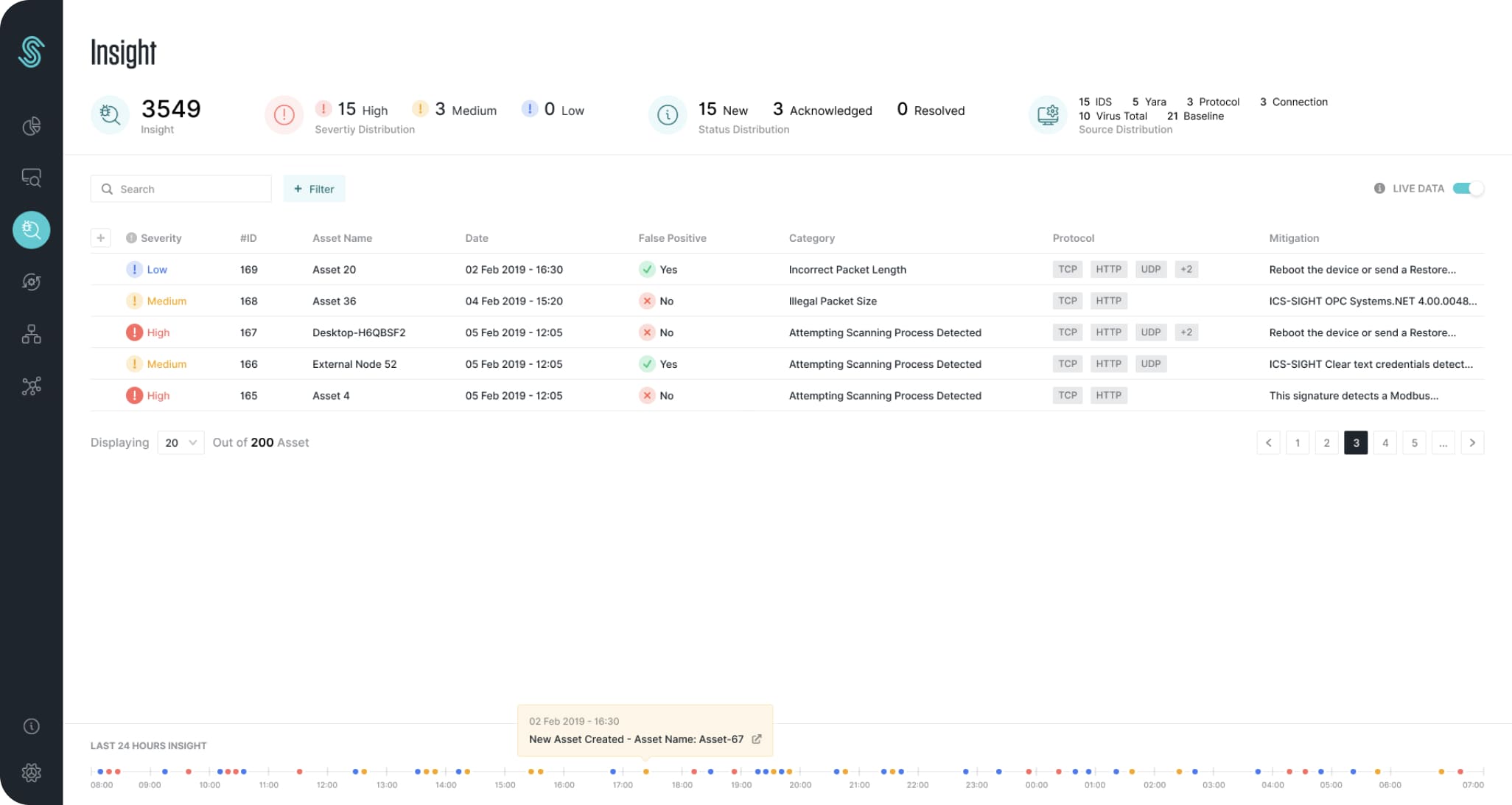
Stay safe with a powerful rule engine and layered warning system
As a cyber security software before everything, one of the ICS Sight’s most powerful side is the layered warning system that has been specially studied. Due to this system, proactive security is provided against current cyber attacks, as well as process, baseline and communication rules can be managed from the same center. In addition to that, the necessary infrastructure has been provided for users to write a specific rule according to the asset, process or protocol. By means of this flexible warning system, specific rules can be written for the needs of each industry and a true cyber defense system can be provided.
ICS SIGHT
Cyber Security Architecture Powered by All Services
The warning system, in which anomaly detection and detection anomalies are shown with the rule engine, is designed quite flexibly not only for cyber attacks with ready rules but also for detection of protocol and device-based anomalies.
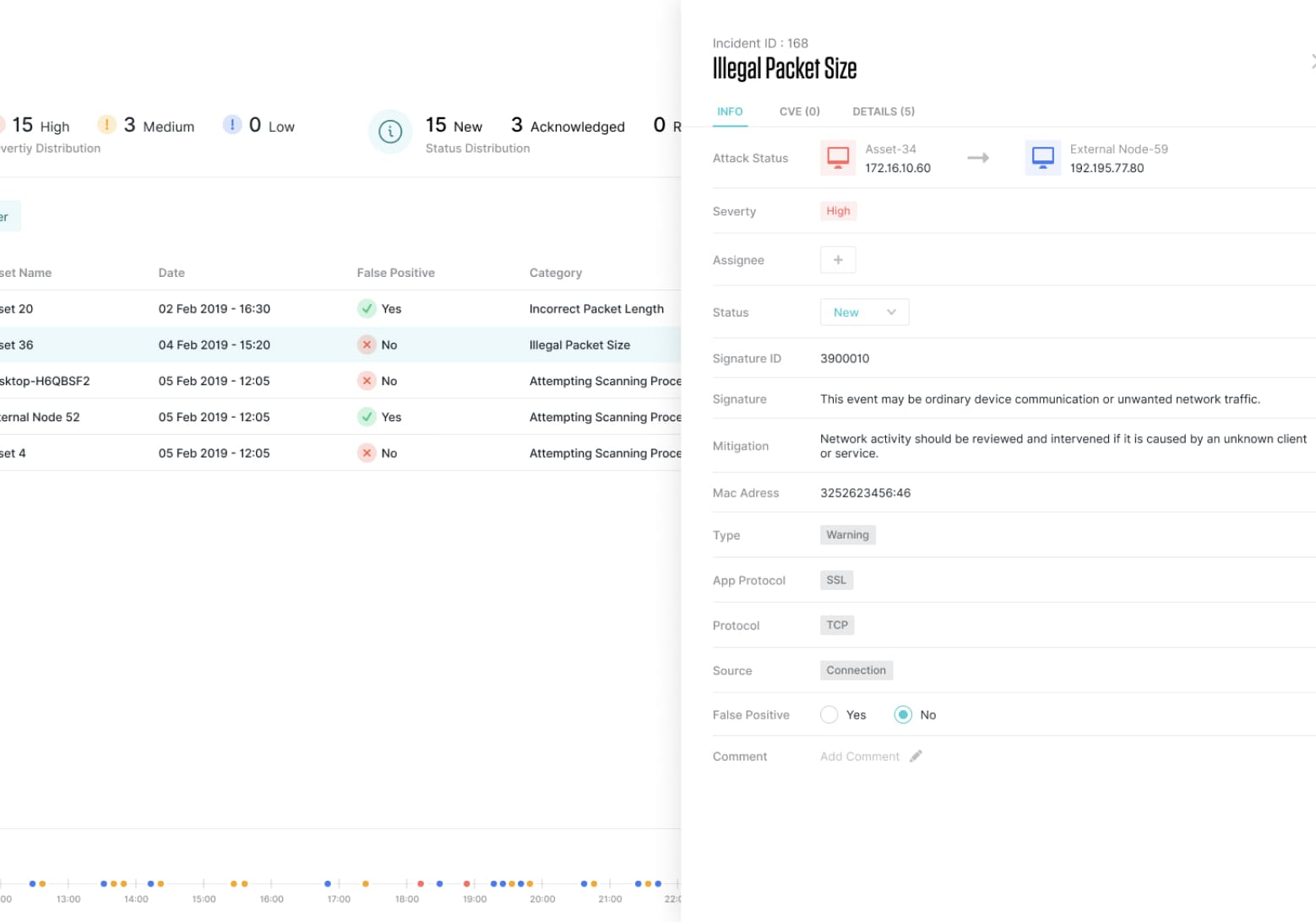
Layered Structure, Flexible Usage
With the help of its flexible structure and layered architecture, regardless of the rule engine, all anomalies detected in the system are displayed in a single interface in a convenient manner with the immediate intervention capability.
Powerful Rule Engine
The rule engine which has strong cyber security rules that can detect thousands of harmful software and attack types, can be configured for the businesses with the rules that can be added by the user in a simple way.
Assigning the Employees According to Alerts
The notifications detected in the critical infrastructure and received in the warning system can be assigned to those responsible and whether the problem is solved or not can be followed up with the feedback received from the system.
PRODUCTS
You Can Browse Our Other Features
Rule Engine
The rule engine which has strong cyber security rules that can detect thousands of harmful software and attack types, can be configured for the businesses with the rules that can be added by the user in a simple way.
Anomaly Detection
The warning system, in which anomaly detection and detection anomalies are shown with the rule engine, is designed quite flexibly not only for cyber attacks with ready rules but also for detection of protocol and device-based anomalies.
Network Mapping
The network map provides a lot of detailed information such as the location of the assets, communication between the assets, possible attack vectors and spoken protocols, as it shows the overall structure of the system.